Iso 27001 Risk Register
- ISO 27001 is the globally accepted standard that offers clients the assurance that the organisation is managing the confidentiality, integrity and availability of information. One of the cornerstones of implementing an ISO 27001-compliant ISMS (information security management system) is conducting an effective information security risk assessment.
- How an ISO 27001 risk assessment works. An ISMS is based on the outcomes of a risk assessment. Businesses need to produce a set of controls to minimize identified risks. Controls recommended by ISO 27001 are not only technological solutions but also cover people and organizational processes.
Although ISO 27001 places strong emphasis on the role of the ‘risk owner’, which pushes risk responsibility to a higher level within the organisation, the asset owner is the logical starting point when compiling an asset register. Risk assessment and impact determination. Once the asset register has been produced, the next step is to. Organisations wishing to achieve certification to ISO/IEC 27001 should note that (as per clauses 8.2 and 8.2 of ISO/IEC 27001) they should carry out information security risk assessments, keep records of those information risk assessments and use the information risk treatment plan derived from the information risk assessments to treat the.

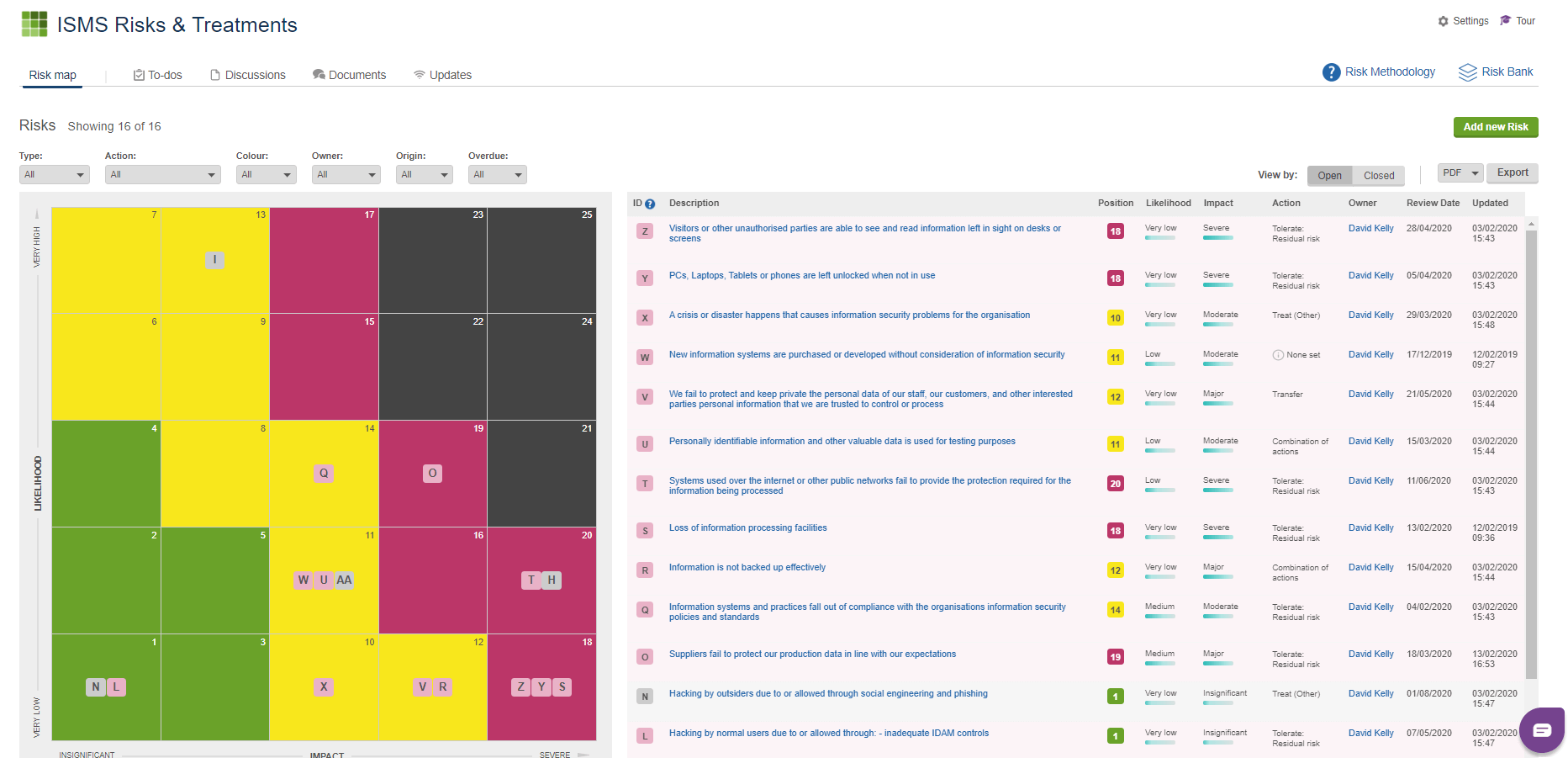
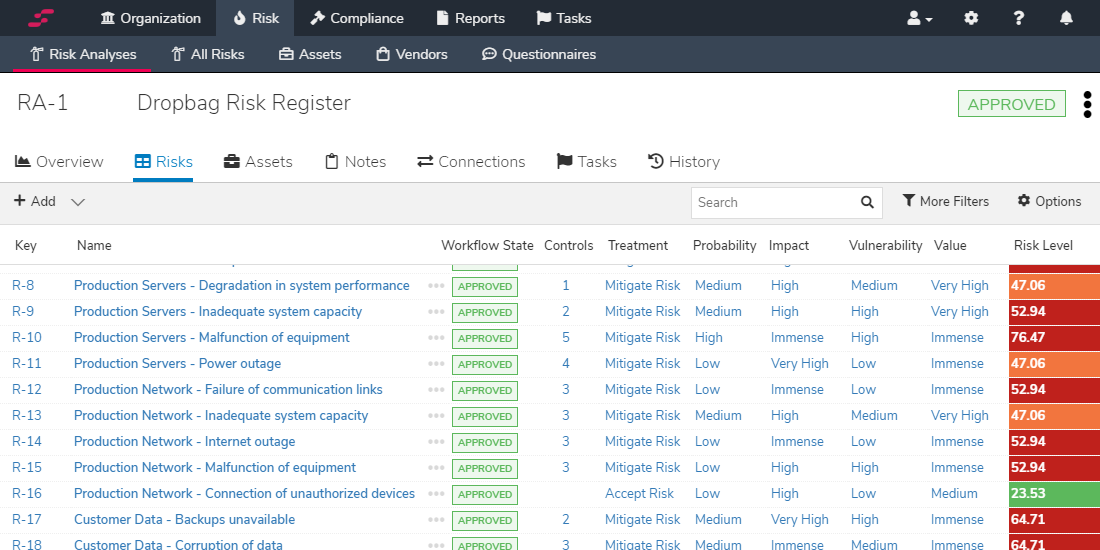
Iso 27001 Risk Register Example
Hi Kevin, welcome to the ISO27k Forum.
You've partly answered your own question. If the analysis is too deep and too detailed, not only will the risk register be extensive but managing, maintaining and simply using it will be problematic. Significant risks may be 'lost among the weeds'. On top of that, you may be spending too much time and effort on analysis, leaving too little left over for treating the risks - and, by the way, learning more about them since risk treatments don't always work out as they should.
Conversely, if the analysis is too superficial/insufficiently detailed, you will probably miss or at least fail to understand significant risks. Risks may be misinterpreted, ignored, or otherwise mis-characterized. On the upside, less analysis means you'll be able to put more of your resources into treating the risks sooner than if you had waited to 'complete' the analysis [hint: it is never 'complete' in the real world!].
Somewhere between those extremes is a happy medium ... but exactly where that is depends on factors such as the nature and maturity of the business and the people involved in the analysis. For example, an organization just setting out on the road towards ISO27k compliance is well advised to pick out and focus on a few 'obvious' information risks first, get to grips with them and treat them, all while gradually gaining experience and maturing. In time, expanding the depth of analysis may be appropriate, particularly for risks that seem to be 'significant', or where incidents and near misses suggest that the risks are worse than they appear, and perhaps weren't even recognized as such. An organization that is critically dependent on information, especially one facing substantial threats and constraints such as legal and regulatory compliance obligations imposed upon it, is in a different position to ... one that isn't!
Aside from the depth of analysis, there's another equally important factor, namely the breadth or scope of analysis. I often rant about cyber-myopia - the over-emphasis on deliberate attacks against networked IT systems, downplaying or ignoring other risks (e.g. incidents with accidental or natural causes, and incidents affecting other forms of information aside from computer data). Thinking more broadly still, information risks are just one class of risks facing the organization: a mining company, for instance, has to deal with health and safety, engineering, commercial, compliance, financial, environmental and other risks, as well as information risks. That bigger picture varies according to the nature of the business, its industry, its owners and competitors etc. Also, the size and complexity of the organization has an influence: information risk management in a diverse global corporation is bound to be different to, say, a hospital.
Oh and another! The method or process of analysis is yet another variable e.g. subjective versus objective approaches, hybrids and experimental methods. There are governance and assurance aspects to this too.
I'll stop there and give others a chance to get a word in, except for one parting comment: there is lots more advice in various ISO27k and other standards, books, methods, websites, webinars, groups etc.
Kind regards,
Gary
_________________________________________________
Gary Hinson
IsecT Ltd., New Zealand
Passionate about infosec awareness, standards and metrics
_________________________________________________
--
You received this message because you are subscribed to the ISO27k Forum.
To post a message to ISO27k Forum, send an email to iso27001...@googlegroups.com or post online through groups.google.com For more information about ISO27k, visit www.iso27001security.com Please respect the Forum's rules at www.iso27001security.com/html/forum.html#TipsAndEtiquette
---
You received this message because you are subscribed to the Google Groups 'ISO 27001 security' group.
To unsubscribe from this group and stop receiving emails from it, send an email to iso27001...@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/iso27001security/f49b3dd8-70dc-4bd5-b50a-486ed30f8cc7%40googlegroups.com.
For more options, visit https://groups.google.com/d/optout.
You've partly answered your own question. If the analysis is too deep and too detailed, not only will the risk register be extensive but managing, maintaining and simply using it will be problematic. Significant risks may be 'lost among the weeds'. On top of that, you may be spending too much time and effort on analysis, leaving too little left over for treating the risks - and, by the way, learning more about them since risk treatments don't always work out as they should.
Conversely, if the analysis is too superficial/insufficiently detailed, you will probably miss or at least fail to understand significant risks. Risks may be misinterpreted, ignored, or otherwise mis-characterized. On the upside, less analysis means you'll be able to put more of your resources into treating the risks sooner than if you had waited to 'complete' the analysis [hint: it is never 'complete' in the real world!].
Somewhere between those extremes is a happy medium ... but exactly where that is depends on factors such as the nature and maturity of the business and the people involved in the analysis. For example, an organization just setting out on the road towards ISO27k compliance is well advised to pick out and focus on a few 'obvious' information risks first, get to grips with them and treat them, all while gradually gaining experience and maturing. In time, expanding the depth of analysis may be appropriate, particularly for risks that seem to be 'significant', or where incidents and near misses suggest that the risks are worse than they appear, and perhaps weren't even recognized as such. An organization that is critically dependent on information, especially one facing substantial threats and constraints such as legal and regulatory compliance obligations imposed upon it, is in a different position to ... one that isn't!
Aside from the depth of analysis, there's another equally important factor, namely the breadth or scope of analysis. I often rant about cyber-myopia - the over-emphasis on deliberate attacks against networked IT systems, downplaying or ignoring other risks (e.g. incidents with accidental or natural causes, and incidents affecting other forms of information aside from computer data). Thinking more broadly still, information risks are just one class of risks facing the organization: a mining company, for instance, has to deal with health and safety, engineering, commercial, compliance, financial, environmental and other risks, as well as information risks. That bigger picture varies according to the nature of the business, its industry, its owners and competitors etc. Also, the size and complexity of the organization has an influence: information risk management in a diverse global corporation is bound to be different to, say, a hospital.
Oh and another! The method or process of analysis is yet another variable e.g. subjective versus objective approaches, hybrids and experimental methods. There are governance and assurance aspects to this too.
I'll stop there and give others a chance to get a word in, except for one parting comment: there is lots more advice in various ISO27k and other standards, books, methods, websites, webinars, groups etc.
Kind regards,
Gary
_________________________________________________
Gary Hinson
IsecT Ltd., New Zealand
Passionate about infosec awareness, standards and metrics
_________________________________________________
--
You received this message because you are subscribed to the ISO27k Forum.
To post a message to ISO27k Forum, send an email to iso27001...@googlegroups.com or post online through groups.google.com For more information about ISO27k, visit www.iso27001security.com Please respect the Forum's rules at www.iso27001security.com/html/forum.html#TipsAndEtiquette
---
You received this message because you are subscribed to the Google Groups 'ISO 27001 security' group.
To unsubscribe from this group and stop receiving emails from it, send an email to iso27001...@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/iso27001security/f49b3dd8-70dc-4bd5-b50a-486ed30f8cc7%40googlegroups.com.
For more options, visit https://groups.google.com/d/optout.
